
HIPAA Compliant Products. Reduced Risk. Guaranteed
We help you build secure, HIPAA compliant products without slowing down development. Overcome HIPAA compliance barriers with Cipher Wall, ensuring top-tier security without the overhead
We have helped many leaders secure their products and will help you secure yours!
Download a Free Copy of Our HIPAA-Ready Product Security Paper:
Proven Expertise in Product Security
Our Staff Helped Many Companies In Healthcare Secure Their Products
forsure.ai


We guarantee you effective results to uplift your product security
Our Services
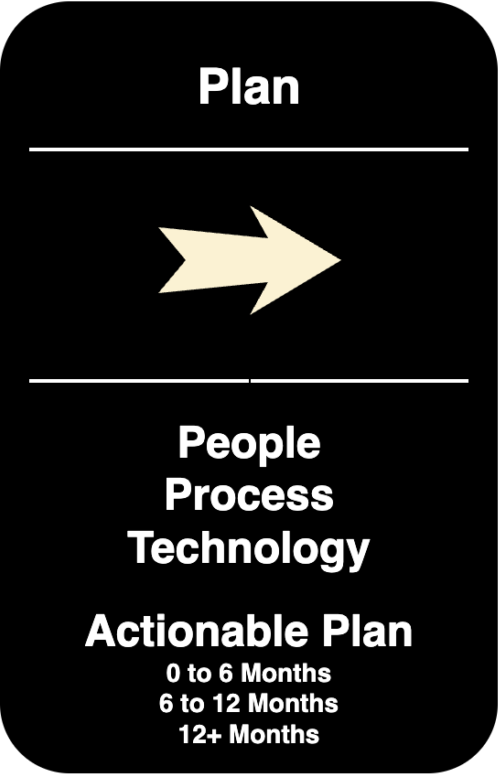
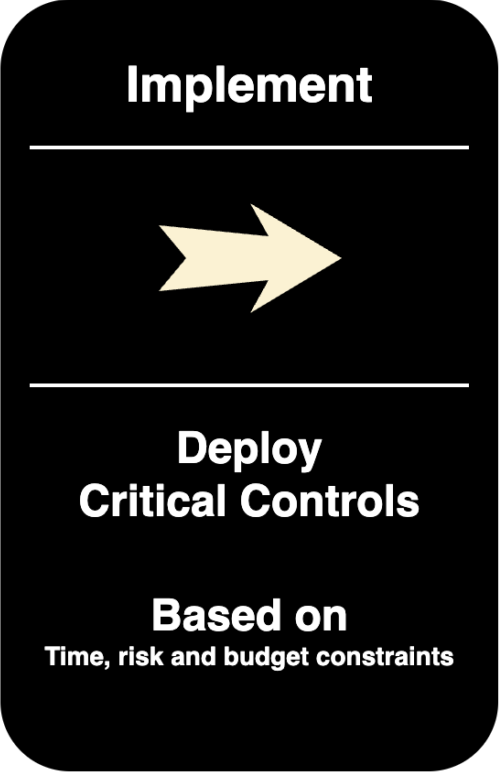
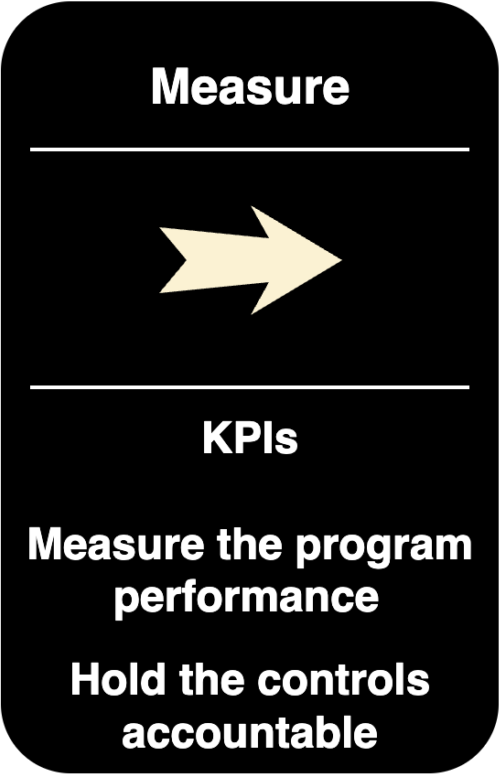
Product Security Programs
– Gap analysis
– Roadmap Building
– Program & Control Implementation
– KPIs & Metric
Pentesting and Remediation
– Conducting pentests
– Fully remediate findings
AI Safety and Security
– Assure AI is not breaking your compliance and security posture
Compliance Readiness
– Fully support your organization through your compliance journey
Our Process is Simple and Effective. Keeping Compliance Embedded from Day One
Whether you are a company with existing product(s)

Or you are an early-stage startup



We’re also here to get you compliance ready

Testimonials
Hear from leaders we have helped before with Product Security
A Message From The Founder
Mohamed (Mody) Mohamed
With 18 years of diverse experience spanning both technical and managerial roles, I’ve had the unique opportunity to observe and solve complex product security challenges across multiple industries. My extensive background allows me to approach problems from various perspectives, offering comprehensive solutions that address the root causes at different organizational levels. You can trust that you’re in capable hands with our team, and here’s why:
• Proven Expertise Across Industries: I’ve helped numerous organizations build and strengthen their product security programs, including industry leaders such as cxLoyalty (a JPMorgan Chase subsidiary), Splunk, Dexcom, Collegeboard, Avaaz, and Illuvium.
• Advanced Education: I hold a master’s degree in cybersecurity from Utica University, an institution recognized as a Center of Excellence by both the National Security Agency (NSA) and the Department of Homeland Security (DHS).
• Top Certifications: I have earned over a dozen high-level certifications in areas such as CISSP, blockchain security, mobile security and pentesting, cloud architecture, and secure software development—ensuring my knowledge stays current and comprehensive.
• Advisory Board Leadership: I serve on the Global Advisory Board for Computer Forensics at EC-Council, one of the world’s premier institutions for security training and certification. Global Advisory Board for Computer Forensics.
• Innovation in Security: I am the patent-pending holder of Covert-Comm, a cutting-edge security solution designed to counter surveillance and enable covert communications.
• Academic Contributions: I have been invited to join the ranks of adjunct professors at two universities through the HackerU program, reflecting my commitment to advancing the field through education.


